Splunk’s passwords can be decrypted.
Splunk provides the means to decrypt the passwords.
Splunk Versions 7.2.2+
Use the show-decrypted CLI command to get the password value.
/opt/splunk/bin/splunk show-decrypted --value $hashYou can also use the show-encrypted CLI command to do the reverse if a need arose.
/opt/splunk/bin/splunk show-encrypted --value changemeSplunk Versions 6.3.0 – 7.2.1
This trick is useful for times where your old admin didn’t share the pass4SymmKey or other “encrypted” fields in the config. This method became possible after 6.3.0 when passwords.conf was introduced.
Splunk Password Basics
Splunk provides a nice write up of how secrets are stored within configuration files on the file system. It’s important to note that when a clear-text password is detected in a “secret” field, the next restart of Splunk will cause this value to become encrypted using the splunk.secret value. This value is generated upon first install and is normally different between Splunk installations, meaning that your encrypted values would be different even if the original clear-text value was identical.
Passwords.conf
Add a passwords.conf file in your favorite config directory, ie. /opt/splunk/etc/apps/search/local/passwords.conf, with the following contents.
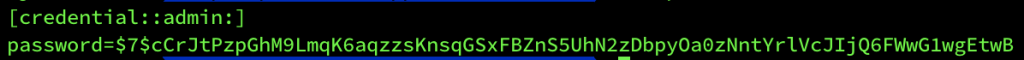
[credential::admin:]
password=<encrypted_value_to_decrypt>The example from my test instance.
Debug Refresh
Perform a debug refresh to force Splunk to load this new file into active config. Perhaps a restart if you’re getting a Forbidden on this link. (Free users)
https://<your_ip>:8000/debug/refresh
Splunk API for Clear Text
Use the Splunk API to view all the passwords (the one you just added) managed by Splunk via passwords.conf.
https://<your_ip>:8089/services/admin/passwords
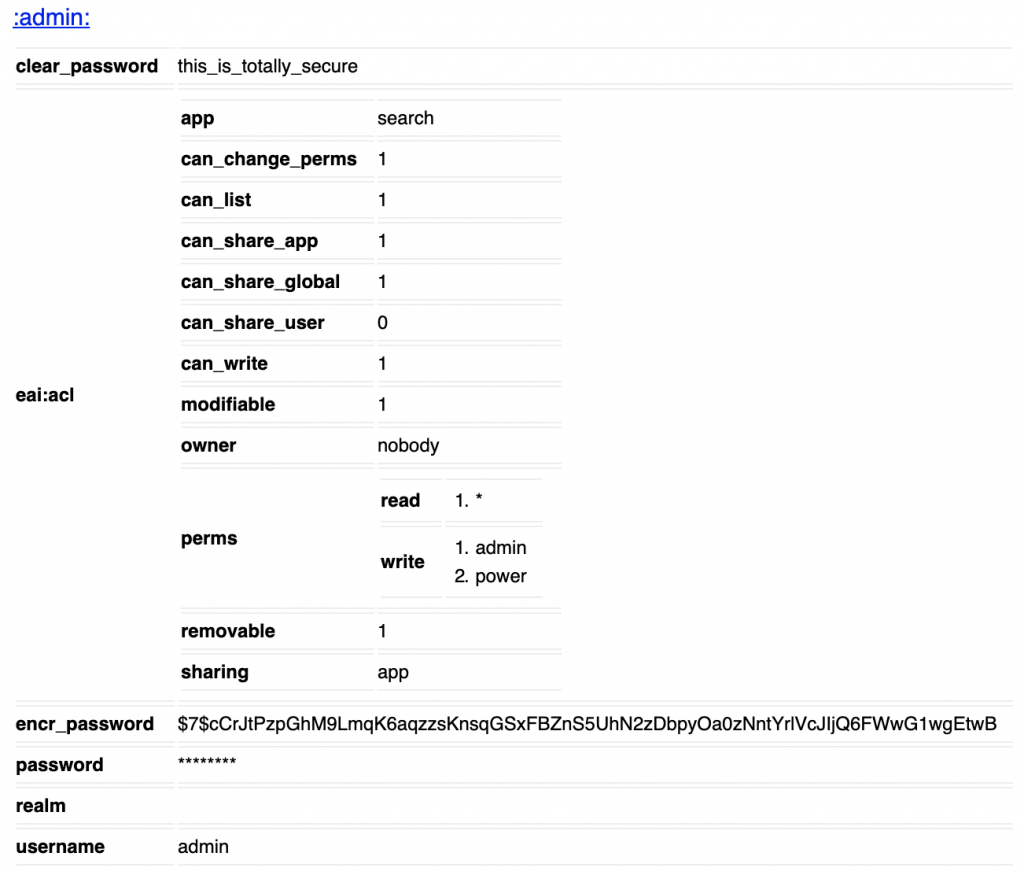
You’ll find the clear-text in the clear_password field.
Hope this helps with recovering an unknown password.
